Network integration
Before designing and building a Network, check out the overview, sample use cases, and main technical concepts.
Once you have your Network concept, start designing and building the necessary components. It is recommended to test and deploy your Network locally (requirements checklist pending), then to Testnet (under development), and finally to Mainnet.
Network Onboarding
Integration with Networks will start with the Testnet launch, but we are already offering support to qualifying launch partners. If you want to build an Network on Nektar, please contact us.
We will review and whitelist your address to allow burning collateral for slashing.
Network onboarding process:
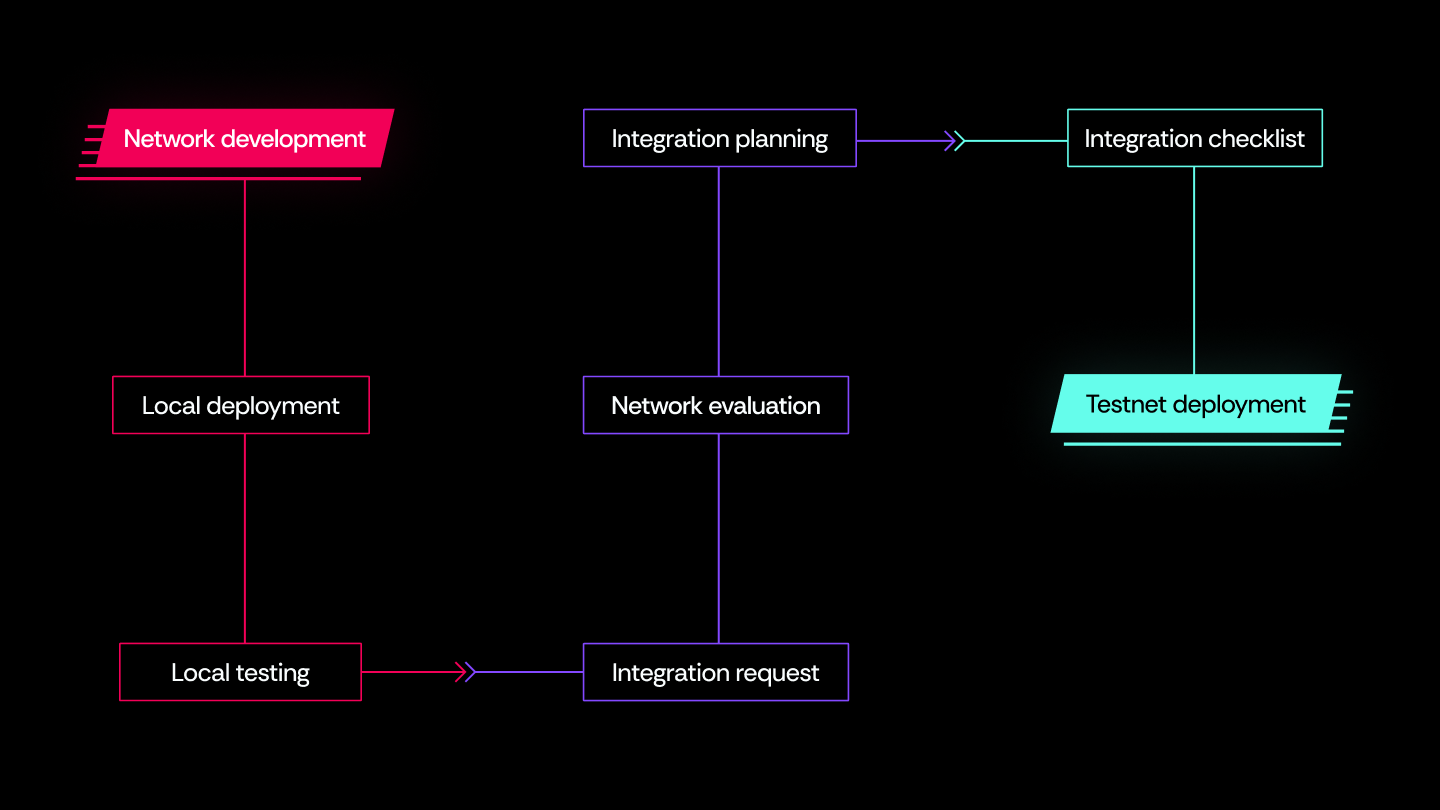
Trust Requirements
Depending on the trust type needed, specify target requirements for:
- Economics: Delegated stake amount (tokens, min/max values, period)
- Decentralization: Number of Operator nodes (geographical and other distribution)
- Ethereum: Number of Ethereum validators
Workflow Definition
Identify the work to be performed, why a distributed network is necessary, and how specific tasks provide the required functionality. Map out the workflow steps from each participant’s perspective.
Typically, a task is submitted to Network contracts with input data, which is then passed to Operators for execution. Responses are calculated, signed, and returned by collecting signatures from network peers.
System Architecture
Create an overarching diagram showing all system components and their interactions, especially between smart contracts and client software.
This helps keep everyone aligned during development, serves as a good introduction in your documentation, and assists Operators during Network onboarding.
Network Design
Network design varies based on your use case. In dual-token staking scenarios, proof-of-stake networks allow community members to support it through staking.
The consensus mechanism ensures the majority of nodes agree on proof validity, which may involve signature aggregation techniques (e.g., BLS) for efficiency.
Set a threshold for the minimum number of Operator responses with signatures and stake percentage required to complete a task.
Client Technology
Choose client technology based on network design and use case—there’s no one-size-fits-all recommendation.
Operators might want to review the source code of your binary to minimize slashing risks for their infrastructure.
Compute Workload
Consider the computational intensity of tasks. For decentralized trust, work should be lightweight, allowing broader participation by less powerful nodes (e.g. verifying zero-knowledge proofs, running light nodes).
Alternatively, use horizontal scaling to distribute computational workload across nodes (e.g. running full nodes of other blockchains).
Operator Documentation
Simplify Operator onboarding with setup documentation and network registration instructions, such as for a Docker container or similar methods.
Provide a user manual detailing trust assumptions, identifying decentralized components, and instructions for using your Network.
Operator Incentivization
Delegators and Operators are rewarded with ETH and your native token. Adjust the proportion: increase the native token’s role as your network matures, and reduce it when you need rapid growth and security consolidation.
Rewards Parameters
Your Network will distribute token rewards to Delegators and Operators. Customize the rewards schedule parameters:
- Token types and amounts
- Credible commitments for future or retroactive rewards
- Distribution type (equal, proportional, vested)
- Commission logic (Operator/Delegator proportion, conditions)
Rewards must be claimed when available, either manually via a web interface or programmatically.
Slashing Conditions
Delegators accept the risk of slashing when restaking with your Network, based on predefined rules.
Design slashing conditions to be provable on-chain. Poorly designed conditions can lead to divergence and systemic risk.
Associate tasks with applicable slashing conditions. They are enforced via smart contracts managing withdrawal credentials for repurposed ETH, making sure that non-compliance will results in slashing.
Design your Network for observability, enabling monitoring, tracing, and logging of requests and responses across its services.
A veto committee can potentially overrule incorrect slashing through multi-sig voting.
Information Security
Implement security measures throughout development:
- Code security audit for smart contracts
- Proper key management for client software
Development Practice
Operators may evaluate your development practices during Network onboarding. Be prepared to show:
- Code change traceability
- Testing suites
- Commit messages and issue tracking
- Technical whitepapers and documentation
Technical Support
Make sure you provide technical support for your client software during network issues. Offer a consistent approach for security updates and release management.