Network use cases
Nektar connects marketplace participants to meet their infrastructure and liquidity needs, enabling a wide range of use cases. Some Networks may focus exclusively on asset sourcing without requiring Operators, while others primarily seek additional compute power without needing collateral from Delegators.
Asset flow
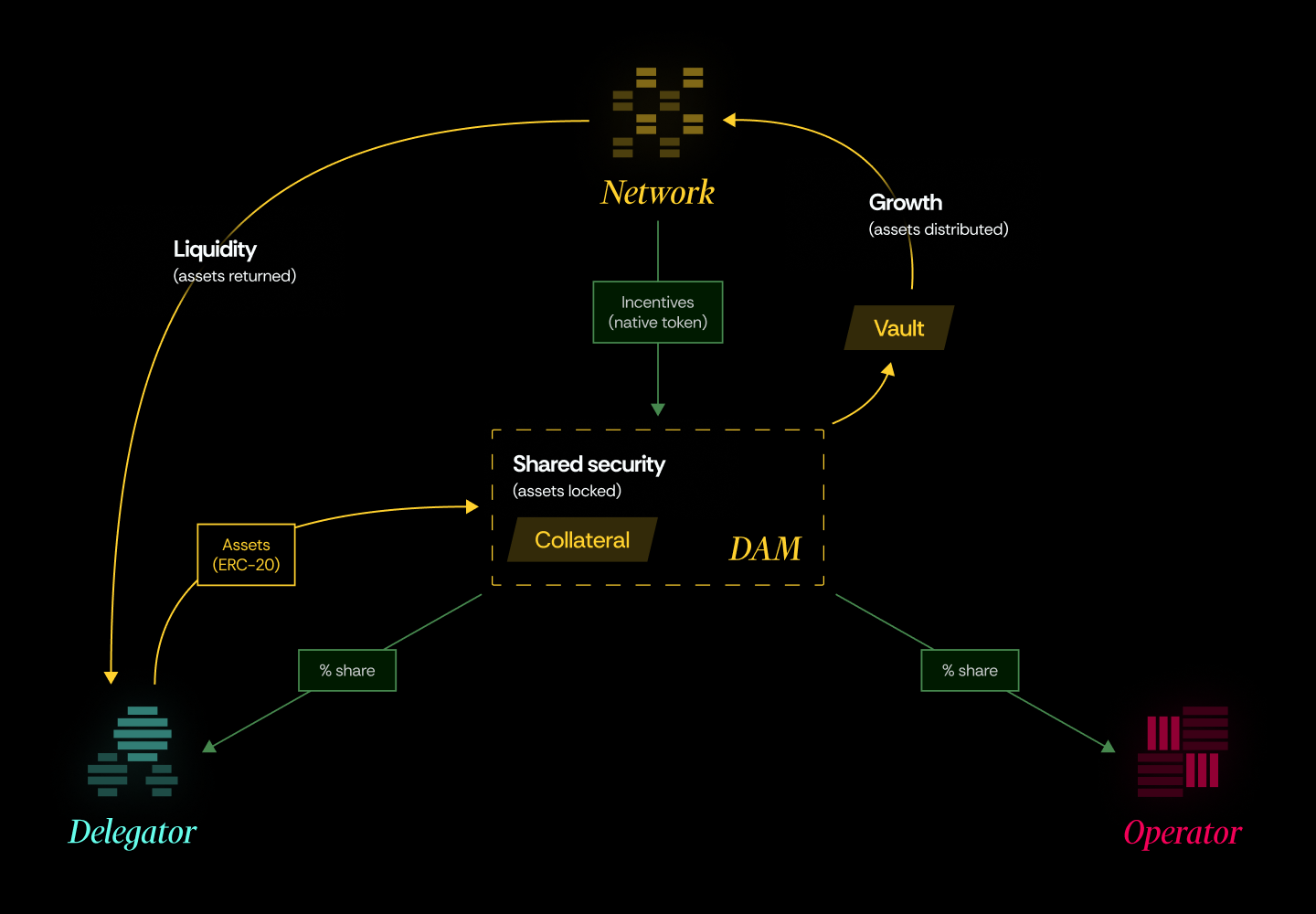
Networks can implement various asset flow scenarios, including:
- Infrastructure: No assets required.
- Liquidity: Assets are transferred to a time-locked vault. Once the lock expires, the funds are moved to a designated smart contract for use previously proposed by the Network in a non custodial and transparent manner. At the end of the Network's interaction in Nektar's lifecycle, the assets must return to the Delegators.
- Growth: Assets are transferred to a time-locked vault, and once the lock expires, the Network can withdraw the released assets. These assets do not return to Nektar.
- Shared security: Assets remain in Nektar as collateral. If Operators behave maliciously, the Network can request assets, which are moved to a time-locked vault for dispute resolution.
Growth and Liquidity scenarios feature atomic withdrawals, whereas collateral DAMs require a two-step withdrawal process (request + claim).
Examples
Explore the sections below to learn more about sample use cases for Networks: